Have you been a victim of logging in on a website that appeared exactly like the bank’s website or any other reputable website but only to discover later that it was not a genuine one?
If yes, then you’ve been the victim of web fakery. This shady practice is more frequent in the modern age and poses a serious risk to our privacy and security online.
In this blog In this blog post, we’ll learn about what is known as website spoofing in greater detail, know the mechanism behind it and discover the actions we can take to safeguard ourselves from such attacks.
Phishing websites and website spoofing:-
Website spoofing is a type of cyber attack that involves creating a fake website that looks and feels exactly like a legitimate one, with the intention of tricking individuals into entering their sensitive information.
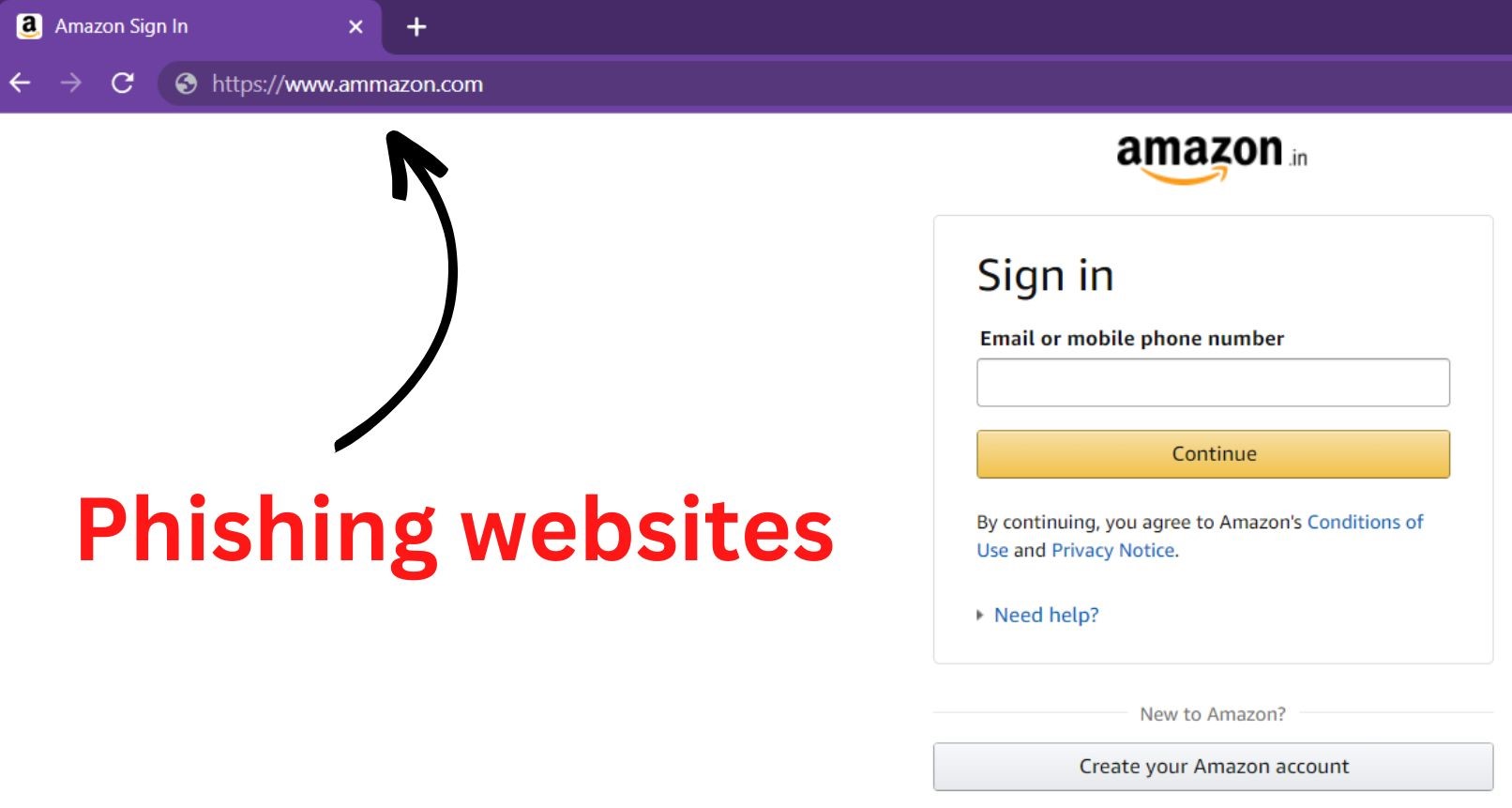
The fake website has been created to mimic the original website in every way including the URL logo, layout, as well as content which makes it nearly impossible to tell the difference from the real one.
The hackers use the information to steal sensitive information, like log-in credentials, bank details as well as personal information that can be later used to carry out malicious activities, such as identity theft fraud and cybercrime.
Spoofing attacks on websites can occur in a variety of forms, such as attacks involving phishing, such as sending an email that contains a link to a fake site or making a false web page that looks like a well-known and trusted site like an online store or a bank website.
In certain cases, attackers could also use browser extensions or other malicious software to redirect users away from the legitimate site to the fake with no knowledge.
Attacks on websites that spoof information can have severe consequences for both companies and individuals, as attackers could use stolen information to commit financial fraud, identity theft and other nefarious activities.
With these dangers, It is crucial that people are aware of fake websites and take the required steps to safeguard themselves from these attacks.
Types of Website Spoofing Attacks:-
There are several types of website spoofing attacks, including:
Phishing Attacks:-
This type of attack involves sending an email or a message with a link to a fake website that looks like a legitimate one.
The attacker may use social engineering techniques to trick the victim into entering sensitive information, such as login credentials, financial information, or personal details.
URL Spoofing:-
This type of attack involves creating a fake website with a URL that is similar to the legitimate one, but with small differences such as an added or substituted letter.
This makes it difficult for the victim to differentiate between real and fake websites.
Session Hijacking:-
This type of attack involves intercepting and taking over an active website session.
The attacker can use this information to access sensitive information, such as login credentials and financial information.
DNS Spoofing:-
This type of attack involves altering the domain name system (DNS) to redirect a user from a legitimate website to a fake one.
The attacker can then use this fake website to steal sensitive information.
Browser Extension Spoofing:-
This type of attack involves installing a malicious browser extension that redirects the user from a legitimate website to a fake one.
The attacker can then use this fake website to steal sensitive information.
Cross-Site Scripting (XSS) Attack:-
This type of attack involves injecting malicious code into a legitimate website, allowing the attacker to steal sensitive information or manipulate the website.
These are some of the most common types of website spoofing attacks. It is important to be aware of these attacks and to take the necessary measures to protect yourself from them.
How to identify a website spoofing attack?
Here are some signs that can help you identify a website spoofing attack:
» Suspicious URL: The fake website could have a URL similar to the authentic one, but with tiny distinctions, like an extra or substituted letter. Beware of URLs that appear like the official site, but with slight differences.
» Request for sensitive information: Legitimate websites typically don’t require sensitive information, like passwords for login or other financial details in the event that it is required to complete the transaction. If a website asks for sensitive information, you should be careful and confirm the legitimacy of the website.
» Poor Layout and Design: Fake websites may have poor layouts and designs as well as grammar and spelling mistakes. Genuine websites typically have professionally designed layouts and content.
» Unexpected Pop-Ups: Fake websites can display unexpected pop-ups or advertisements that request sensitive information. Beware of any sudden ads or pop-ups.
» Unsecured Connection: Fake websites may not have a secure connection, as indicated by the lack of a padlock icon in the browser’s address bar or a “https” in the URL. Legitimate websites typically have a secure connection.
» Unusual Requests: Websites that are fake may request that you install plugins or software or redirect you to a different site in a sudden manner. Be aware of any suspicious requests.
If you are aware of these warning signs You are able to take the appropriate steps to guard yourself against an attack that spoofs websites.
It is also recommended to keep your browsers and software up to date and to utilize security software, like anti-malware and antivirus tools to guard against trolling attacks.
Protecting yourself from website spoofing attacks:-
Here are some steps you can take to protect yourself from website spoofing attacks:
» Verify the authenticity of the website: Check the URL carefully and ensure that it’s identical to the one you usually use. Check for any changes, like an extra or substituted letter.
» Use secure connections: Find the icon for the padlock within the address bar in your browser. Also, confirm that the URL begins by a “https.” This indicates that the site is secure.
» Be cautious of unsolicited emails: Be cautious of email messages that are not from you and contain hyperlinks to websites, particularly when they request sensitive information. Beware of clicking on links within emails or messages sent from unidentified or suspicious sources.
» Keep your browsers and software up-to-date: Keep your software and browsers up-to-date to ensure any security flaws are fixed.
» Uuse anti-malware and antivirus software: Use anti-malware and anti-virus software to guard against spoofing attacks on websites as well as other forms of malware.
» Avoid using public Wi-Fi: Avoid using Wi-Fi networks in public areas when you are entering sensitive information such as banking information, since these networks could be insecure and vulnerable to attack.
» Enable two-factor authentication: Two-factor authentication is recommended, in the event that it is available, for online accounts, to provide an additional level of protection.
By following these guidelines You can shield yourself from attacks using spoofing on websites and ensure that your personal information is safe.
In addition, it is advised to be careful when submitting sensitive information online. It is also recommended to periodically check your accounts for any unusual activities.
Conclusion:-
Website spoofing poses a significant threat to security online, and it’s important that you are aware of indicators of a fakery attack and take the essential steps to ensure your security.
This means confirming the legitimacy of the website and using secure connections. beware of emails that are not legitimate as well as keeping your browser and software up-to-date, by using anti-malware and anti-virus programs, avoiding Wi-Fi networks that are public, and making sure you enable two-factor authentication when there is.
If you are vigilant and take the appropriate steps, you will be able to protect yourself from spoofing attacks on websites and keep your private information protected.
Other Related Links:-